We are a white-listed service provider...
Much of what we deliver is business sensitive. Our clients trust it stays that way, that’s why we’re family-style close with those we do business with. Trust is a big deal.
A lot of what we do comes via referral. Here is why:
How to Avoid Microsoft 365 Price Increases and Keep Your Old Subscription Plan
Microsoft is quietly upselling its 365 subscribers with a 40% price hike, tied to limited AI features many don’t need. But there’s a hidden way to keep your subscription at the original price – no AI, no extra costs. Learn how to dodge this unnecessary increase and keep your plan exactly as it was. Thank…
iPhone notification sound is loud – how to fix
How to Reset Your iPhone’s Notification Volume: A Simple Guide Have you ever noticed that your iPhone’s notification volume just doesn’t seem quite right? Maybe it’s too loud, or perhaps it’s too soft, and adjusting the volume slider just isn’t doing the trick. One common and effective solution to this issue is resetting the notification…
Never Store Passwords on Your Computer: A Cautionary Tale
This is for anyone who’s ever thought “storing passwords on my computer is convenient” – including your web browser. It’s a wake-up call based on a real-life experience that shows why it’s a risky practice. The Story The author fell victim to a social engineering attack and their computer was compromised. Hackers hijacked their YouTube…
What to Do When Microsoft Outlook for Mac/iOS Stops Receiving Emails from Google Accounts
Microsoft Outlook is a popular email client that is used by millions of people around the world. However, there are some instances where Outlook may stop receiving emails from Google accounts. This can be a frustrating problem, but it is usually easy to fix. One common solution is to remove and re-add the Google account…
How to Change Your Facebook Password
Your Facebook password is the gatekeeper to more than just your account – it can open doors to other accounts, so it’s important to keep it strong and secure. If you think your password might have been compromised it is important to change it and you can do so easily in a few steps. Here’s…
The Importance of Setting Your Homepage Title and Description
The homepage title and description are the first things that both search engines and users see when your website appears in search results. They serve as a brief summary of your website’s content and purpose. Boosting Visibility A well-crafted title and description can make your website stand out in search results, increasing the likelihood that…
The Zelle Transfer Scam
Scammers are always looking for new ways to steal your money, and the Zelle transfer scam is one of the latest and most dangerous. In this scam, the scammer will email you pretending to be from your bank or credit union. They will claim that there was a problem with your recent Zelle transfer, and…
Brother HL printer offline
If your Brother HL printer is cable connected to your network and suddenly appears offline the fix could be exactly like you’d expect – simple. Have you first checked these points: Power is on and the LCD panel on the front is displaying something (other than an error message), The ethernet cable hasn’t been damaged…
Arlo camera stopped recording motion detection
If your Arlo camera suddenly stopped motion recording after previously working fine, there is a straightforward fix. This has been tested and used on the Arlo Pro 3 Spotlight camera several times now. There are a couple preliminary steps to confirm before taking this action. First: Confirm your account subscription is active/valid, From the app,…
Upgrade your cyber security in 5 minutes
Get done what you’ve been putting off in two easy steps to give yourself a huge head-start against cyber attack by ensuring you have a password manager and 2FA/MFA (multi-factor) protection on your accounts. In the same way you lock the door to your home to prevent unauthorised access, the cyber world requires the same…
How to defeat business cyber security
The weakest link in business cyber security are those running the business – it’s team. The most robust systems are only as strong as those operating it. This is about one specific threat — the “Inside Job.” What is an Inside Job? An Inside Job is when an employee or contractor covertly accesses your company’s…
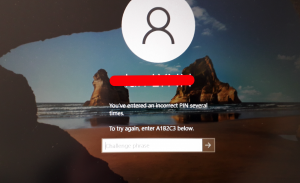
Windows: You’ve entered an incorrect PIN several times
Trying to log into your Windows 10 computer you get the message: You’ve entered an incorrect PIN several times. To try again, enter A1B2C3 below – and that’s still not logging you in, right? The reason behind this is varied although a common denominator around July/August 2021 relates to a Microsoft software update. To log…
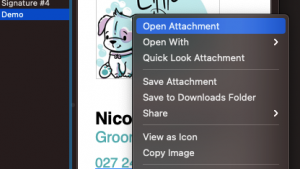
Hyperlink an image in Apple Mail signature
Making a functional and hyperlinked email signature in Apple Mail is very easy, and very limited. You can easily hyperlink text, you can’t hyperlink images (as of 2020). There is always a workaround. For text; simply highlight it, right-click (control-click) and look for ‘Add Link’ –> paste/edit the link. The same ‘can’ be done if…
Pioneer SC LX87 with DC voltage at the amplifier output
If you get the flashing MCACC LED indicating that the systems diagnostic has detected DC voltage at the amplifier output there are a couple easy checks before it needs servicing. This same method applies to some other PIoneer amplifier units. First, check all fuses are intact. Second, perform a power fault reset by pressing and…
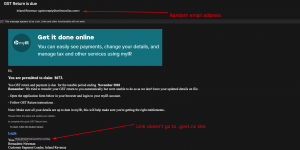
IRD GST scam email
The need to treat any email with caution has been further heightened with a clever attempt to phish IRD credentials – presumably in an attempt to hijack your personal details. Titled: ‘GST Return is due’ is the first warning sign, given the date the email was sent. The use of legitimate artwork adds to the…
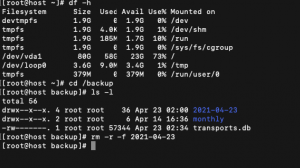
Delete a directory and files from a Linux system
Here is how you delete files and folders or directories from Linux based operating systems in one simple step rm -r -f (followed by the directory name). Such a simple command. First you’ll need to be logged in with root access, or use sudo rm -r -f (then the directory name) The rm is short…
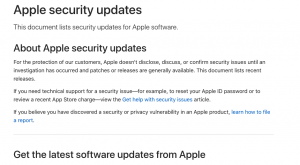
Mac, iPhone, iPad, iCloud, Apple watch user? Update now to plug a security vulnerability
Issued on 26 January 2021 Apple have updated software supporting their products and services that closes a recently exposed and exploited vulnerability. Which is? The ability for a malicious application that can elevate privileges to gain higher level access and control critical files/functions. The exploit isn’t specific and affects different devices in different ways. If…
Raspberry Pi as Network Attached Storage (NAS)
Content on this page is intended to compliment the article series published The Shed magazine (To Server or Not to Server – What Was I Thinking? Or, A Sheddies Guide to the Data Galaxy, by Nigel Young), as a way of delivering more in-depth detail and update changes to install and configuration of software used/described.…
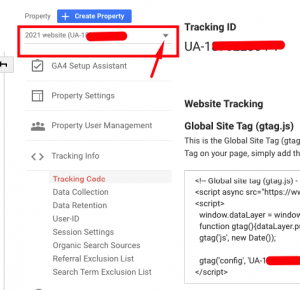
How to generate Google Analytics UA code in new GA4 platform
When Google Analytics upgraded in October 2020 the ability to create a UA- ID for website tracking became a bit hidden (by a lot). Luckily there is a simple series of steps to support websites that only accept UA- code tracking over use of the new gtag.js method. From your Google Analytics ‘Admin’ goto the…
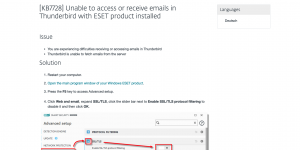
Thunderbird mail not working after 1 December?
If you’re using Eset security on your PC and Thunderbird for an email client they will have stopped working on 1 December. The simple workaround was to disable Eset (webmail and email filtering). There is a permanent solution and it’s pretty simple. It was all to do with Eset replacing their security certificate. Thunderbird didn’t…
Have you done enough to be compliant for the Privacy Act 2020?
If you’re in business the Privacy Act 2020 affects you Shortly the 2020 version of the Privacy Act comes into effect (1 December). Its purpose is to catch-up a lot of the ground between its initial 1993 deployment and the current way of the world and bring New Zealand closer to the European standard General…
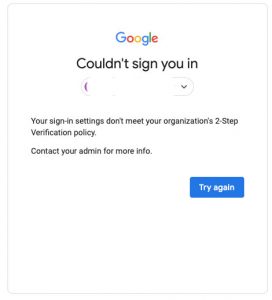
Error when logging into Google account: Your sign-in settings don’t meet your organization’s 2-Step Verification policy
Updating to Google’s login security is preventing authorised access for some users. Try again won’t work either. It is easy to resolve. First you need to log into the master Google account via admin.google.com – the Admin console. Log into the account you’re trying to access. It will now ask you to enter one of…
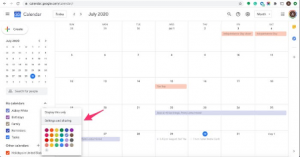
Microsoft Outlook natively supports Google calendar on Mac not on PC
If you use Google Mail and its associated calendar, they work a treat using Outlook on macOS to share your calendar across devices however if you’re a PC user there are a few extra steps. ** Update: I’ve been using a freeware app in a couple instances that sorts this right out. More details at…
Don’t use Time Machine with your NAS/Network storage
What seems like a great idea will deliver great heartache when you need that Time Machine backup and the only or most up-to-date copy is in a network storage location. The heartache will start when you can’t access that network drive location, when you’re doing a system restore following a catastrophic failure. You’ve suddenly got…
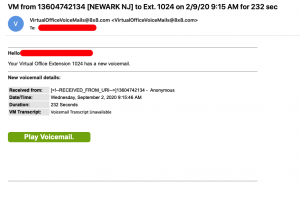
Watch out for voicemail emails
Today a new email notification of a voicemail arrived – that proved to be illegitimate. Like all phishing instances, this was very cleverly done, right down to the sending of the email to spoof as being legitimate. Making it even more convincing, the URL contained in the email tied it to the sending platform –…
Securing your website with https:// is not enough
Unless you’ve recently had your website security upgraded, chances are it is vulnerable. For most websites there is a momentary window of opportunity for hackers to bust it open if they test its ability to redirect from the http:// to https:// address. It is a cat-and-mouse game of shoring up against hackers, for them to…
Is your email account scam resistant?
Knowing how reliant your business is on email requires you be one step ahead of the scammers. That starts with using a premium level service provider and, if you’re using a mail service attached to your domain name, that it is configured to deflect spam and scams. What used to be ‘okay’ in terms of…
Do not click the link in the email!
Did you get an email from Apple about purchasing something from their App store? Take a good look at it and have a good think. Most of all, don’t click the link! That it appeared in my junk box was the first clue that was where it was meant to be. It looks like the…
Troubleshooting: Trusting your gut to find the solution
How often does the light-bulb moment happen and you suddenly realise what you need to do to and fix the fault in front of you? Usually when you’ve given up and gone on to something else, right? It was a lesson I learned early in life – where the answer, or path to finding the…
How we are paying to take down scammers
Are your online viewing choices feeding those who are taking down scammers and their call centres? It doesn’t take too much digging to find that is exactly what is happening. From busted refund call centres to sophisticated share trading schemes, the background publicity of seeing these networks taken down has bred a multi-million viewer and…
Netflix email scam
The ever-growing rise in email scams is taking another twist with their level of complexity increasing in an attempt to defeat filtering and first-glance credibility tests. Netflix are victim to an interesting scam that was worth digging a little deeper on. First clue was the email ended up in the Junk folder – that’s the…
Use Zoom? You’ll need a password
Edited 7 April: more details below: As of Sunday 5th April 2020, Zoom teleconferencing requires use of a password to enter a meeting room. A knee-jerk response to address security concerns and the rise of Zoom-bombers, the password step has stone-walled the majority of users. Oblivious account users are wondering why people aren’t joining regular…
Hacking spikes and one easy way to lock down your website, now
Disappointingly but not surprisingly I’ve seen a large increase in the number of website hacking login lockouts in the past week. It’s only a matter of time before traditional lines of defence are beaten – that’s why I’m enforcing the really simple extra layer of Two-Factor Authentication (2FA or TFA) on client sites, now. For…
MYOB blocked from running?
A recent update by Windows has caused heated headaches in the MYOB community with a few Windows 10 users experiencing the ‘This app has been blocked for your protection’ message. “No. It was working fine yesterday, it should work fine today.” That’s a simple and reasonable thought. Luckily there is a relatively simple solution, several…
Facebook not previewing your website posts?
When you drop a website post link into Facebook does it populate with the post title and featured image, like you’d expect? While there could be many reasons behind this, one possible solution could be as simple as your DNS settings. Facebook scrapes a preview of website posts based on the AAAA DNS record (IPv6).…
Why your website has to be mobile friendly
You’ve probably seen evidence of it every time you encounter someone aged 18-25 – they’re spending so much time each day staring at their mobile device. Statistics show time they spend attached to their phone has nearly doubled in three years. In 2012 average use was 1.88hours/day, in 2015 that had increased to 3.26hrs/day. Those…
Time-lapse photography trade secret
Here is the no-brainer tell-all on what makes for the ultimate time-lapse camera operation to capture the images that will save hours of post-editing to remove the sea-sickening variations and deliver a smooth result – every time. Since I first started in 2010 I’ve learned a lot of hard and heart-breaking lessons. I’ve had plenty…
Why you need to protect your computers power source
Inevitably at some stage the primary source of power to your computer will be cut – and if you are in the middle of something important you can be sure there will be data loss or corruption. That is why you need a UPS. Not the postal service kind – the one that keeps your…
Brushed with CryptoWall 3.0
Recently a client had ransom message appear on their computer right while they were completing a task for a client of their own.It was a spine tingling moment. What do you do? You’re trying to serve your own customer and suddenly your computer makes you freeze – that your next move could delete everything on…
Life in the cloud is beautiful
The whole ‘cloud’ term has long been a pie-in-the-sky target for business users as a method of storing and securing precious data and files. As the dominant service providers (Google, Amazon, Dropbox, Microsoft and Apple as examples) offer cheap cloud storage the shift to storing valuable data offsite has become more affordable. Equally; as data…
Is your website really secure?
The fastest way to get your email address added to spam lists is to have it intercepted by someone ‘sniffing’ insecure web data traffic.Website security comes with so much jargon it is often left to chance in the hope those hosting/looking after your site will be your defence against foul.First; consider your own circumstance:Does your…
Why you will love the person who told you to backup your files
As if lightning can’t strike twice another client has just found (luckily) the value of having data files backed up and why they loved heeding lessons learned by others.The cost was a couple hundred dollars by the time they factored in the specialist help. A paltry cost given what they now have.Everything had been going…
Backup backup backup
Three words you hear time and time and time again. Such a cliché and yet we all know its importance. Here is where I pulled myself from an embarrassing situation – thanks to a backup I found safe on my remote drive.Unfortunately during a shutdown/startup I had an audio file corrupted that I was working…
What to do when you get a computer virus
Today revealed a client with the CrypotoWall 3.0 virus on their computer.Computer viruses are real and a timely reminder on steps we should all have in place to safeguard against the attempts of others to interfere with our setup.It’s a necessary reality and in many ways an excellent way of ensuring we treat our data…
The #1 top-tip when installing software
We’ve all faced the dilemma, and sometimes it’s even out of frustration – to install a new piece of software so we can just get on with it. Along with that is a #1 golden rule that for a few seconds of attention will frequently save you hours of heartache later – especially if you…
Staying ahead of the scammers
It may seem a little alarmist yet history proves daily the website that rests is the one that gets put to rest. Aside from being buried in the ever growing internet ‘noise’ the ever growing scammer/hacker trends require pro-active steps to keep your web presence safe.Aside from back-door Content Management System (CMS) access and bolted-door…
The 12 Website MUST Haves
Here are 12 items a website MUST have if it is to be of use to your target market. A domain name people remember – Your website name has to be as short as possible and as easy to spell as possible. Make it easy for your visitors! Mobile capable – You might be shocked…
Done-for-you-websites
Here is what’s contained in our done-for-you website solution If you’re starting out or run a small website this email will give you a basic outline on the prime services we include in our done-for-you website package, where you provide the basic site contents (copy), images, branding, colour palette and any specifics you need included.…