Posts by Lance
How to defeat business cyber security
The weakest link in business cyber security are those running the business – it’s team. The most robust systems are only as strong as those operating it. This is about one specific threat — the “Inside Job.” What is an Inside Job? An Inside Job is when an employee or contractor covertly accesses your company’s…
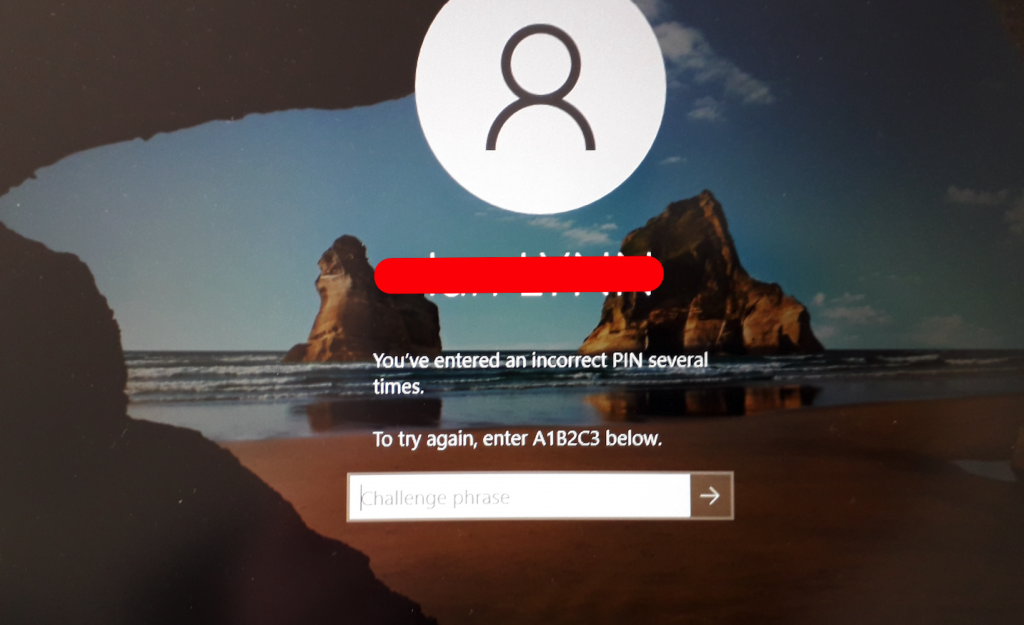
Read MoreWindows: You’ve entered an incorrect PIN several times
Trying to log into your Windows 10 computer you get the message: You’ve entered an incorrect PIN several times. To try again, enter A1B2C3 below – and that’s still not logging you in, right? The reason behind this is varied although a common denominator around July/August 2021 relates to a Microsoft software update. To log…
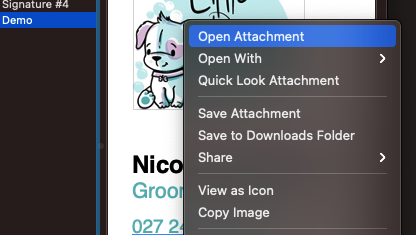
Read MoreHyperlink an image in Apple Mail signature
Making a functional and hyperlinked email signature in Apple Mail is very easy, and very limited. You can easily hyperlink text, you can’t hyperlink images (as of 2020). There is always a workaround. For text; simply highlight it, right-click (control-click) and look for ‘Add Link’ –> paste/edit the link. The same ‘can’ be done if…
Read MorePioneer SC LX87 with DC voltage at the amplifier output
If you get the flashing MCACC LED indicating that the systems diagnostic has detected DC voltage at the amplifier output there are a couple easy checks before it needs servicing. This same method applies to some other PIoneer amplifier units. First, check all fuses are intact. Second, perform a power fault reset by pressing and…
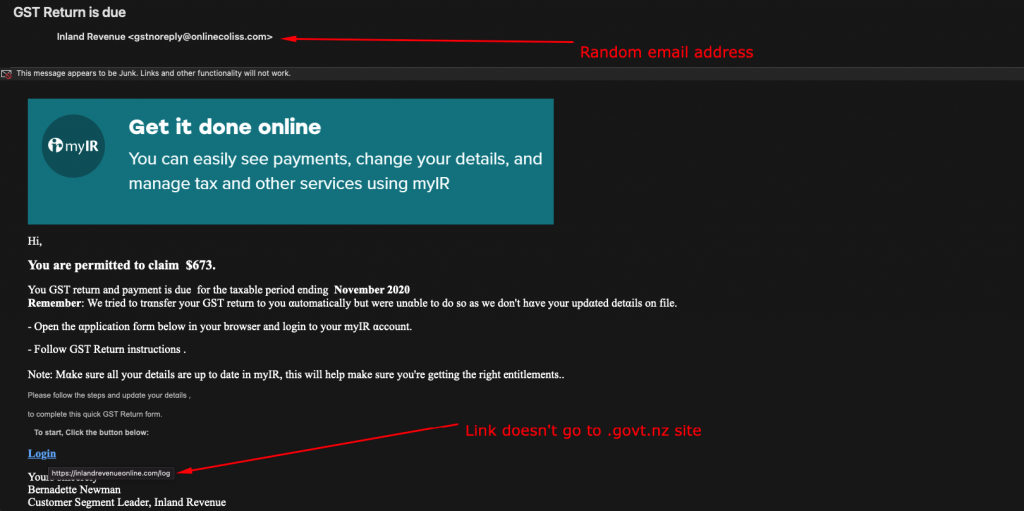
Read MoreIRD GST scam email
The need to treat any email with caution has been further heightened with a clever attempt to phish IRD credentials – presumably in an attempt to hijack your personal details. Titled: ‘GST Return is due’ is the first warning sign, given the date the email was sent. The use of legitimate artwork adds to the…
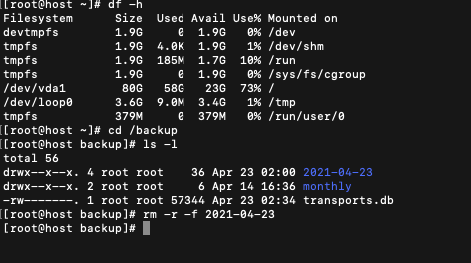
Read MoreDelete a directory and files from a Linux system
Here is how you delete files and folders or directories from Linux based operating systems in one simple step rm -r -f (followed by the directory name). Such a simple command. First you’ll need to be logged in with root access, or use sudo rm -r -f (then the directory name) The rm is short…
Read MoreMac, iPhone, iPad, iCloud, Apple watch user? Update now to plug a security vulnerability
Issued on 26 January 2021 Apple have updated software supporting their products and services that closes a recently exposed and exploited vulnerability. Which is? The ability for a malicious application that can elevate privileges to gain higher level access and control critical files/functions. The exploit isn’t specific and affects different devices in different ways. If…
Read MoreRaspberry Pi as Network Attached Storage (NAS)
Content on this page is intended to compliment the article series published The Shed magazine (To Server or Not to Server – What Was I Thinking? Or, A Sheddies Guide to the Data Galaxy, by Nigel Young), as a way of delivering more in-depth detail and update changes to install and configuration of software used/described.…
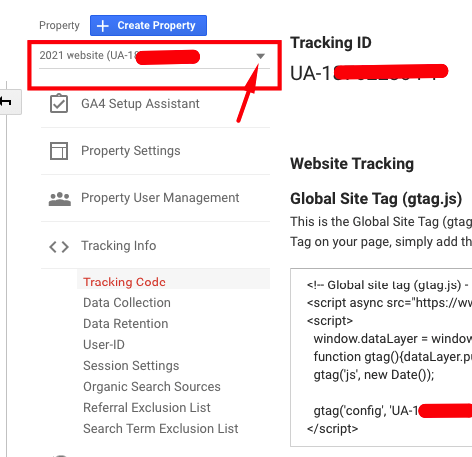
Read MoreHow to generate Google Analytics UA code in new GA4 platform
When Google Analytics upgraded in October 2020 the ability to create a UA- ID for website tracking became a bit hidden (by a lot). Luckily there is a simple series of steps to support websites that only accept UA- code tracking over use of the new gtag.js method. From your Google Analytics ‘Admin’ goto the…
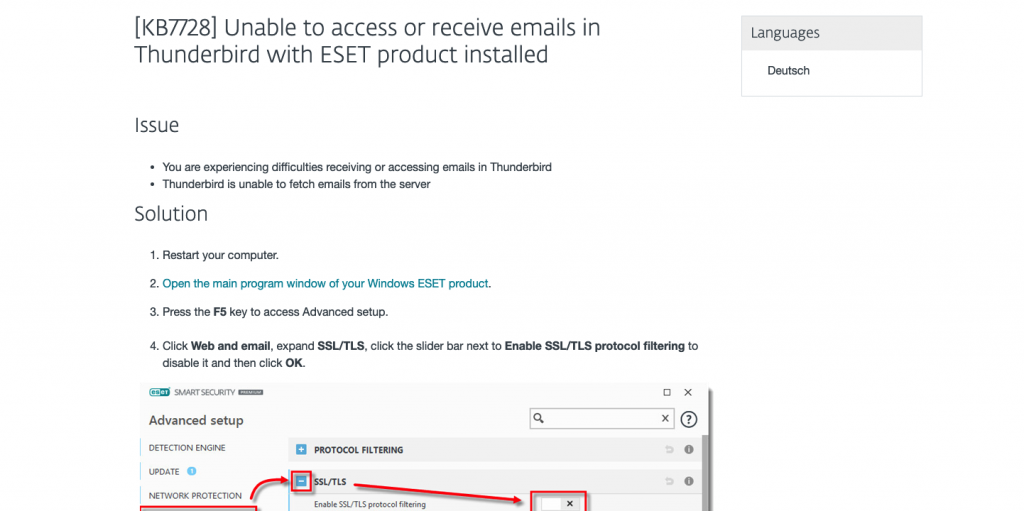
Read MoreThunderbird mail not working after 1 December?
If you’re using Eset security on your PC and Thunderbird for an email client they will have stopped working on 1 December. The simple workaround was to disable Eset (webmail and email filtering). There is a permanent solution and it’s pretty simple. It was all to do with Eset replacing their security certificate. Thunderbird didn’t…
Read More